
Could ‘Circle Spoofing’ Be Ingenious Hackers?
Last Friday we brought you the story of a series of mysterious AIS displacements that had analysts baffled as to their cause. Bjorn Bergman, a researcher with the West Virginia-based nonprofit organization SkyTruth, had said that his search for an explanation was hampered by a lack of “commonality between the vessels and incidents.” The most recent observation involved a number of vessels that were reportedly circling in waters northwest of San Francisco, but in actuality were in various physical locations around the world. The phenomenon was so curious to the learned few that the Resilient Navigation and Timing Foundation (RNT) had expressed its hope to hear from people who might have ideas or insights that could help solve the mystery. Personally, the crew at Latitude 38 were just as baffled as the experts. However it seems some of our readers have insights that may prove valuable in the explanation of the reported ‘circle spoofing’ mystery.
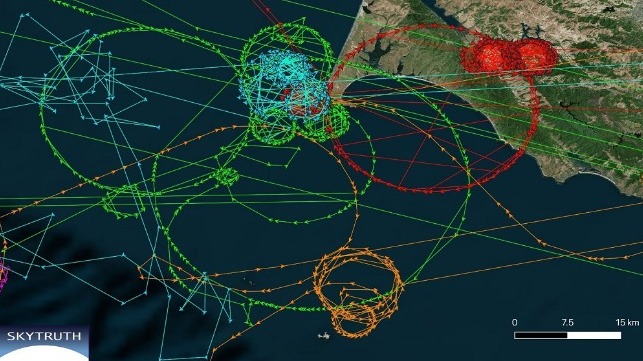
One-time sailor turned game developer Scott Goffman says he’s currently working on a project in which he inadvertently replicated almost the exact opposite scenario from what he thinks may have resulted in the now-nicknamed “AIS crop circles.”
“I’m a game developer currently working on a naval combat game, and just last week I was fixing a bug where enemy ships were being generated inside of a circle radius instead of along the circle’s edge,” Scott said. “Basically the exact opposite problem as in my hacker theory, but based on the same mistake.”
The mistake Scott was referring to is hidden inside his theory that the circles are the result of hackers learning how to intercept and spoof GPS data.
Scott’s theory looks like this:
- They’re choosing random ships to test on (hence the variety of ship types).
- They’re intercepting the positions reported by those ships (either from the satellites or, more likely, on the terrestrial servers where the data are then stored).
- They’re replacing those positions with their own.
- Their code for replacement involves their picking a new location (in this case, near San Francisco).
- They then apply a random offset in a circle around that point. But they had a bug in their code! They meant to choose a random point within a range of their chosen positions, but accidentally generated a random point at a range from their chosen position.
So they did something like this:
var angle = _random.Next() * (Math.PI * 2);
var x = _originX + (_radius * Math.Cos(angle));
var y = _originY + (_radius * Math.Sin(angle));
return new Point( x, y );
Which Scott says “looks like it would do the job, but the alleged hackers had forgotten to randomize the radius. I would bet that shortly after that test they fixed the bug, and their subsequent tests haven’t been noticed.”
Coming from someone who grew up crewing on his father’s sailboat, and is now developing a naval combat game, it stands to reason that Scott has some knowledge to support his theory. However he too is interested in hearing other readers’ thoughts on the seemingly random location issue.
We’re keen to hear from our readers as well. So far no one in our ‘circle’ has provided a better or even plausible theory, so if you have one, let us know; we’d love to hear from you.

Iran has a major interest in AIS spoofing, to keep the sanctioned oil shipments from being tracked. North Korea has similar motivations. Both have large groups of state-sponsored hackers.
Background: I am also a software developer and an avid sailor.
I buy the radius randomization bug explanation, it makes a lot of sense. I’m also thinking it’s also possible that they were trying to be funny and draw something, although I can’t quite pick up the outline of a picture here.
As to how they would do it, that seems pretty easy, and no GPS spoofing needed. AIS is unencrypted, GPS position is self-reported, and it is all transmitted over VHF, you would just need a computer connected VHF transceiver or antenna to broadcast custom data and you could fake being anyone. A bit of digging and I found this article that explains the weaknesses in the AIS protocol (they actually drew letters with the data points): https://www.pentestpartners.com/security-blog/hacking-ais/
If the data is recorded somewhere, you could possibly look at all of the AIS data points to see if there are two sources of transmission (the actual ship and the spoofed transmission). However, it is also possible that the actual ship wasn’t broadcasting at the point in time where they were spoofing them.
As to why? Anyone’s guess. Anywhere from someone thinking they are cute and “having fun”, to a hacker testing out a system to create chaos in the AIS system — difficult to say.